Integrate JumpCloud with FileCloud
As an administrator you can integrate these two systems so that your JumpCloud users can access their FileCloud account without having to enter their credentials a second time.
JumpCloud’s is a cloud-based platform
|
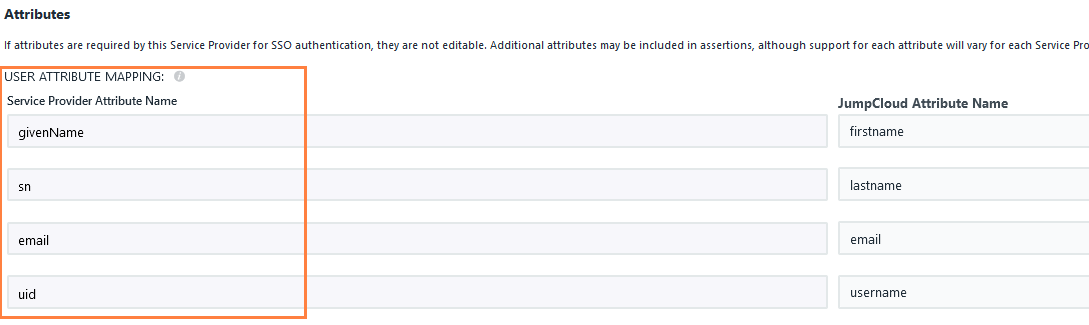
In this integration scenario:
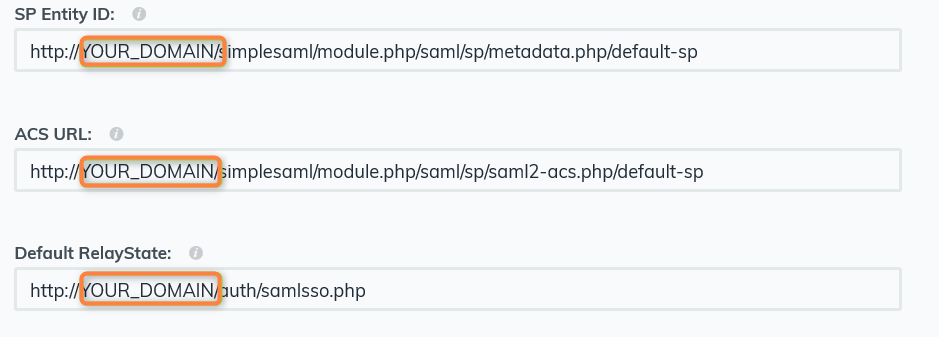
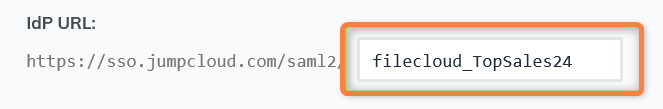
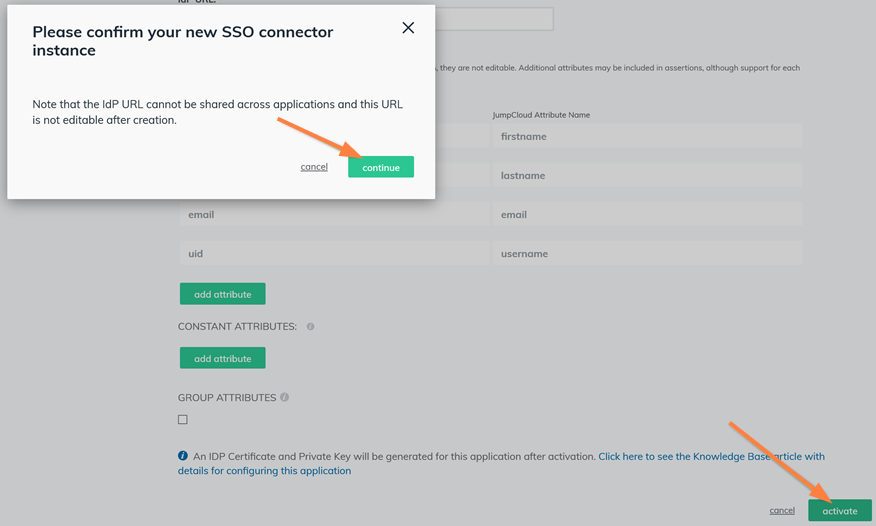
- JumpCloud must be configured as an Identity Provider (IdP)
- FileCloud will act as the Service Provider (SP)
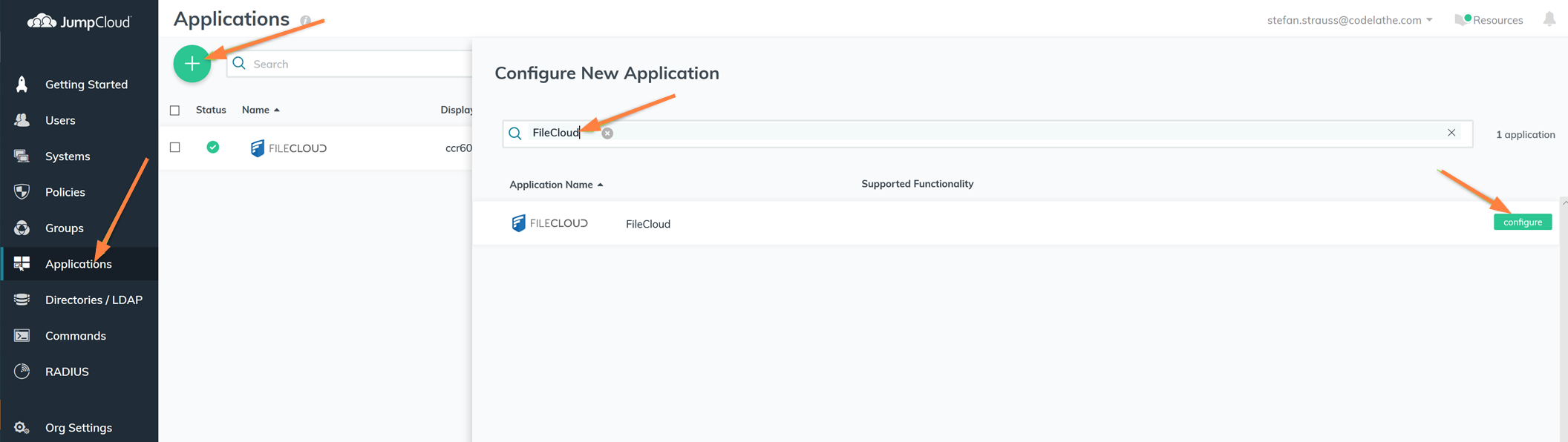
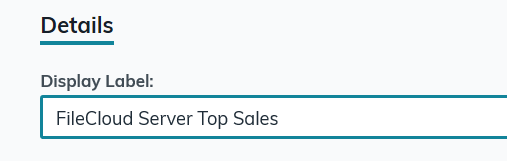
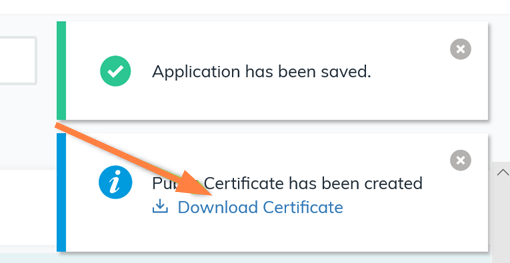
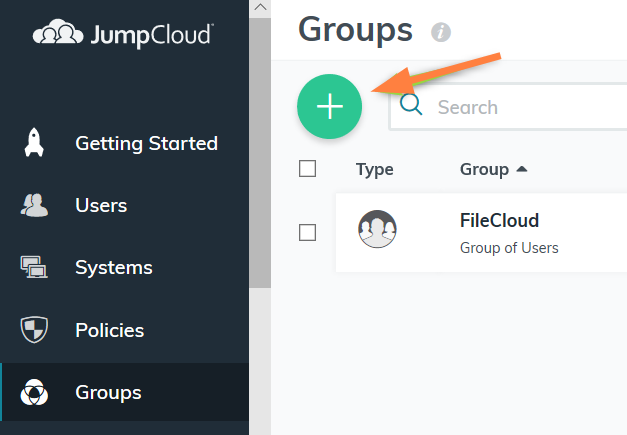
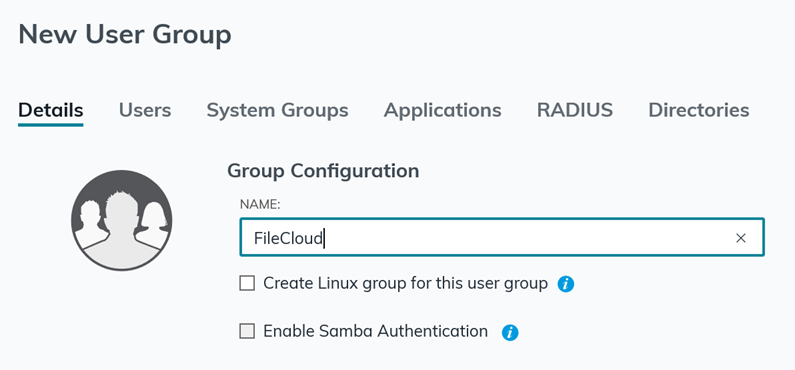
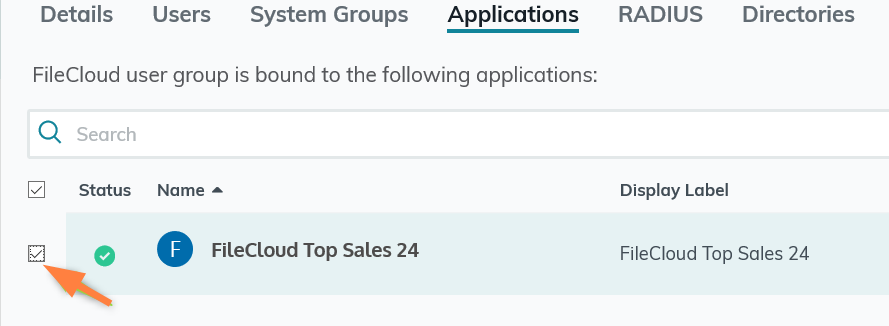
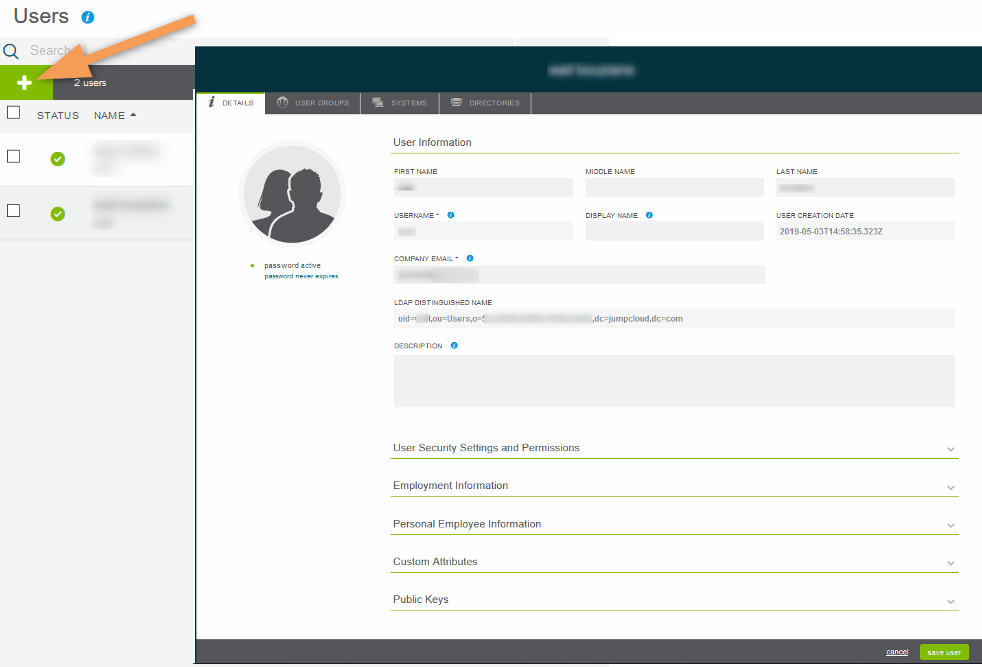
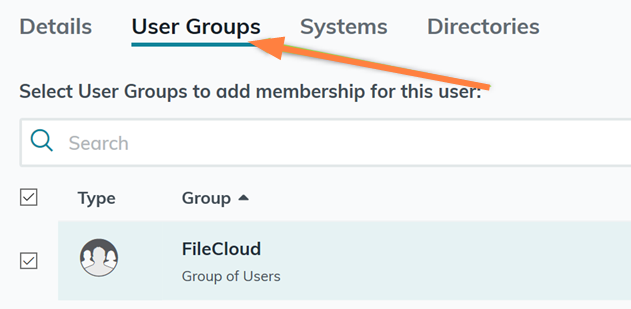
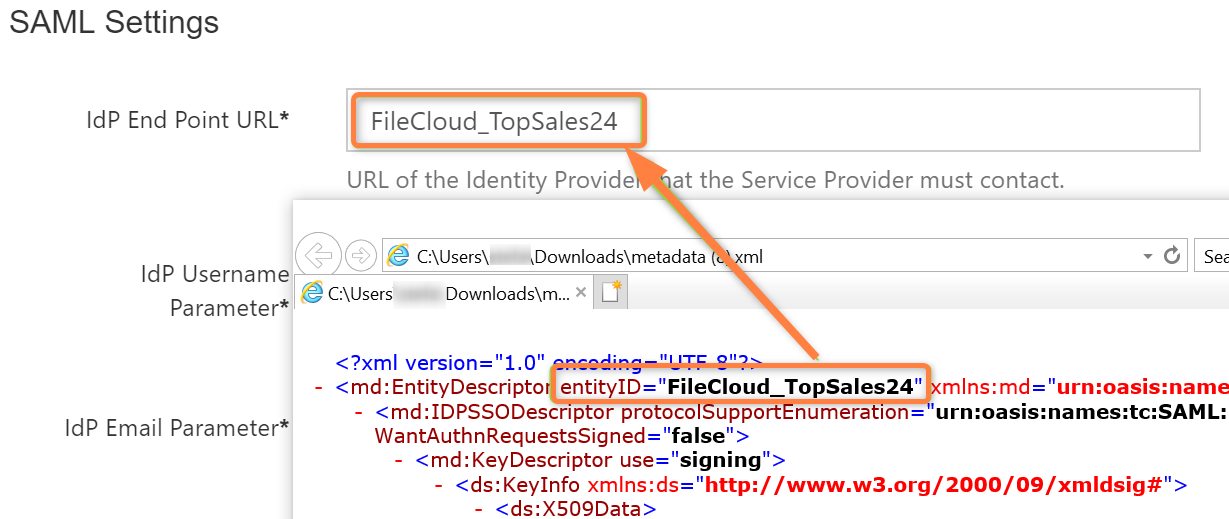
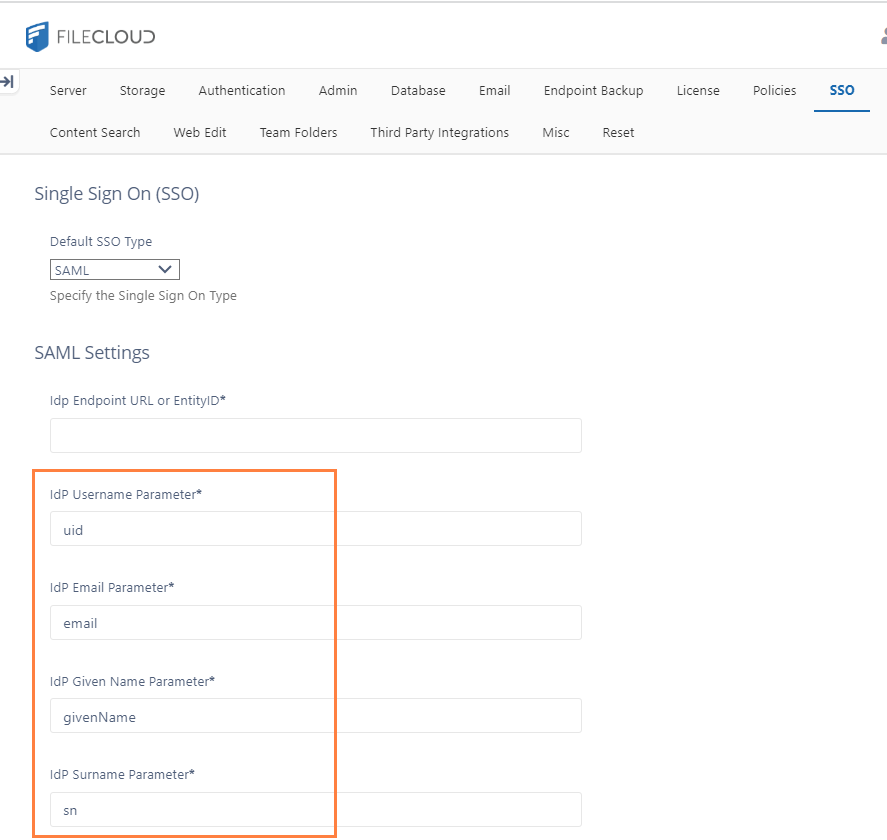
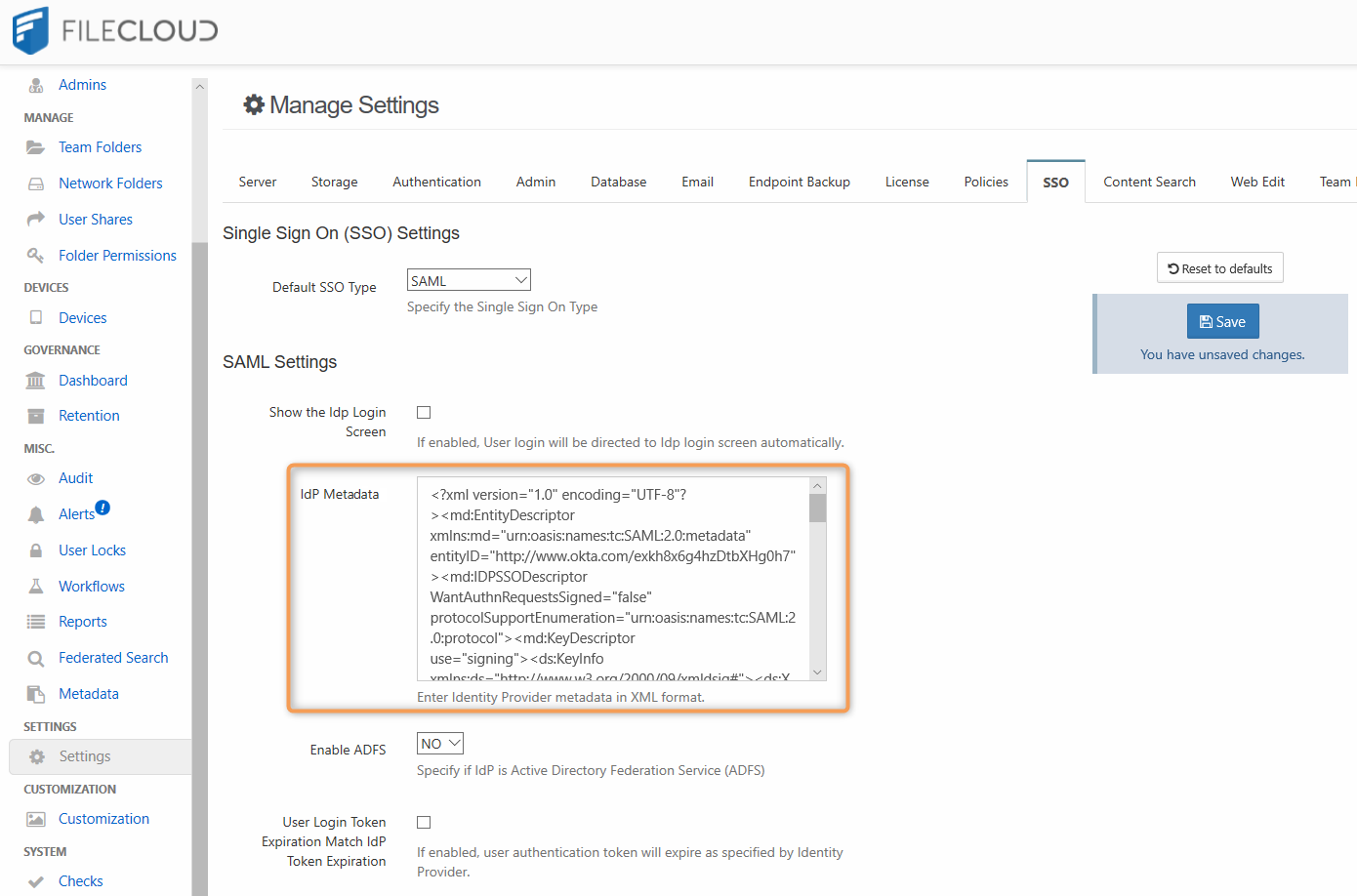
Configure FileCloud with JumpCloud
Now you can start using the Single Sign-On with JumpCloud from FileCloud!