SAML Single Sign-On Support
Note: As of FileCloud Version 20.3.2, to achieve high availability, you can configure FileCloud to support multiple memcache servers.
You can use SAML SSO to control the authorization and authentication of hosted user accounts that can access FileCloud Web based interface.
- SAML is an XML based open standard data format for exchanging authentication and authorization data between parties.
- FileCloud supports SAML (Security Assertion Markup Language) based web browser Single Sign On (SSO) service
- FileCloud acts as a Service Provider (SP) while the Customer or Partner acts as the identity provider (IdP). FileCloud SAML SSO service is based on SAML v2.0 specifications.
SSO Login Diagram
The following process explains how the user logs into a hosted FileCloud application through customer-operated SAML based SSO service.
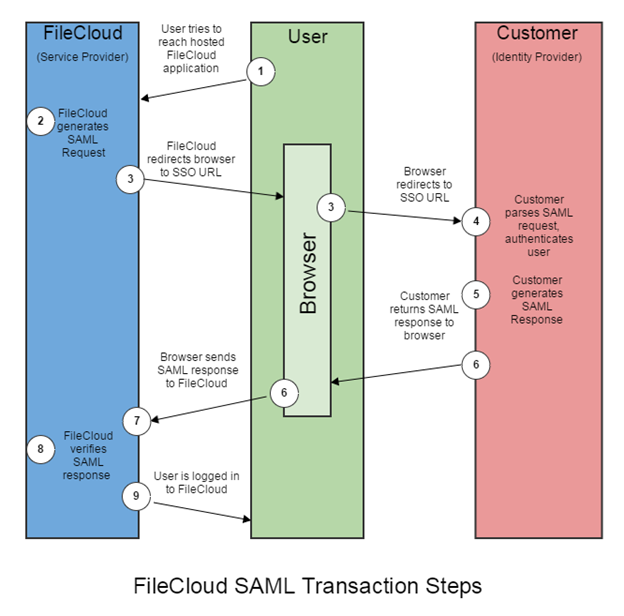
- The user attempts to reach the hosted FileCloud application through the URL.
- FileCloud generates a SAML authentication request. The SAML request is embedded into the URL for the customer’s SSO Service.
- FileCloud sends a redirect to the user’s browser. The redirect URL includes the SAML authentication request and is submitted to customer’s SSO Service.
- The Customer’s SSO Service authenticates the user based on valid login credentials.
- The customer generates a valid SAML response and returns the information to the user’s browser.
- The customer SAML response is redirected to FileCloud.
- The FileCloud authentication module verifies the SAML response.
- If the user is successfully authenticated, the user will be successfully logged into FileCloud.
When the IdP successfully authenticates the user account, the FileCloud (SP) authentication module verifies that the user account exists in FileCloud.
If the user account does not exist in FileCloud, then a new user account is created and the user is logged into FileCloud.
SSO Configuration Steps
In order to successfully configure SAML SSO, the following steps must be followed.
Configuring the Apache server requires you to add the Alias directive to the simplesaml.php configuration file.
Pre-requisite: The mcrypt module must be installed on the FileCloud Server.
- In Windows, it should be installed by default.
- In Linux, if mcrypt is not installed, it must be installed
To add the Alias directive:
Use the following table to understand the typical entries in Linux and windows.
You can change these settings if the FileCloud is installed under a different WEB ROOT Folder.
Windows
Navigate to the following directory
c:\xampp\apache\conf\extra
Open the following file for editing
httpd-filecloud.conf
Add the following line at the end of the file
Alias /simplesaml "/xampp/htdocs/thirdparty/simplesaml/www"
- Save the file.
- Open the FileCloud Control Panel.
- Use the control panel to stop and start the Webserver.
Linux
Go to the following directory:
/etc/apache2/sites-enabled/
Open the following file for editing:
000-default.conf
Add the following line within <VirtualHost *:80> for HTTP connection or <VirtualHost *.443> for HTTPS connection. You can place it under the line DocumentRoot /var/www/html.
Alias /simplesaml /var/www/html/thirdparty/simplesaml/www --→ (Ubuntu 16.04 and higher versions) Alias /simplesaml /var/www/thirdparty/simplesaml/www --→> (Ubuntu 14.04 and lower versions)
To restart the apache webserver, run the following command:
/etc/init.d/apache2 restart
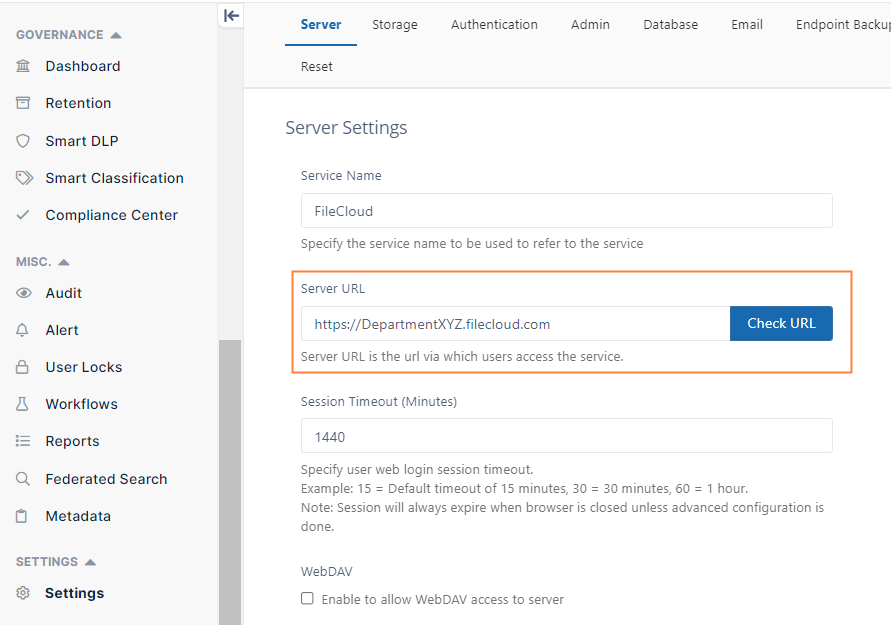
- In the admin portal, go to Settings > Server.
- In the Server URL field, confirm that your URL begins with HTTPS.
- Click Check URL to make sure your URL is valid.
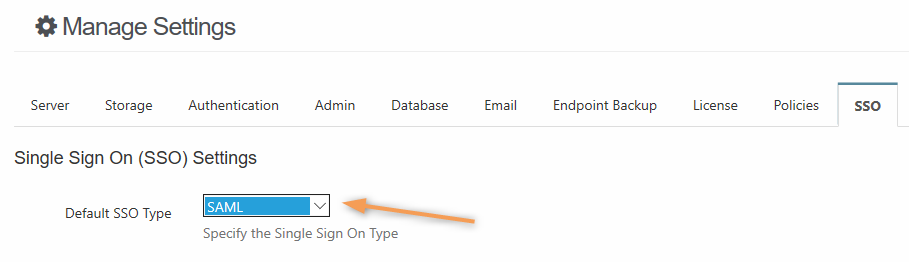
To set the SSO type in FileCloud:
Log into the FileCloud admin portal.
In the left navigation panel, click Settings.
Select the SSO tab.
In Default SSO Type, select SAML.
Note about Active Directory Federation Services (ADFS) Support:
When SAML SSO Type is selected and ADFS is enabled in FileCloud:
- FileCloud will act as a Service Provider (SP)
- FileCloud also acts as a claims aware application.
As a claims-aware application, FileCloud:
- Accepts claims in the form of ADFS security tokens from Federation Service
- Can use ADFS claims to support Single Sign On (SSO) into FileCloud
To specify the identity claims that are sent to the FileCloud refer to the IdP Configuration section below.
When ADFS is used, the IdP (Identity Provider) in these instructions refers to Active Directory Federation Server.
To configure IdP settings in FileCloud:
Log into the FileCloud admin portal.
In the left navigation panel, click Settings.
Select the SSO tab.
In Default SSO Type, verify it is set to SAML.
Set other parameters according to your IdP settings.
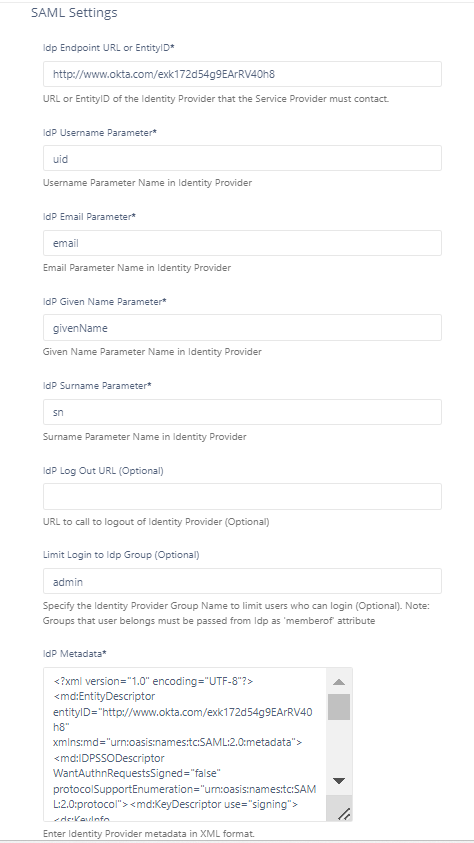
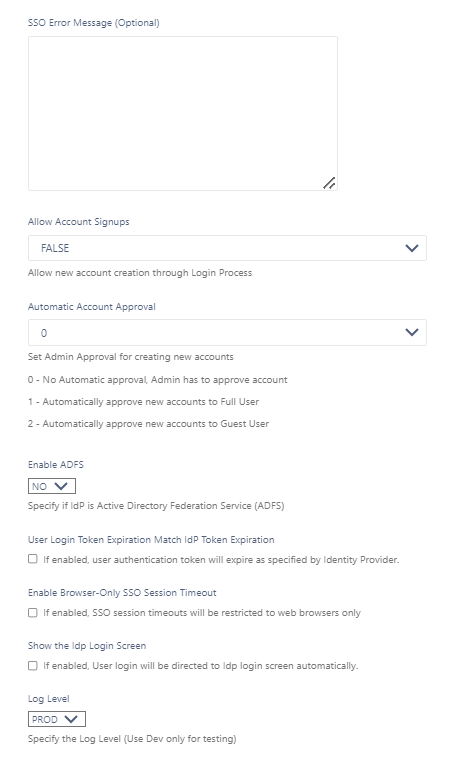
Use the following table to understand the IdP settings.
| FileCloud Parameters | IdP Settings | ADFS as IdP Data can be obtained from Federation Metadata |
|---|---|---|
| IdP End Point URL | Identity Provider URL | Identity Provider URL (Entity ID) |
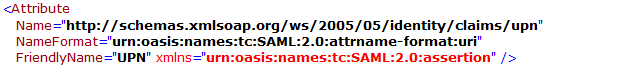
Idp Username Parameter | Identifies the Username (must be unique for each user)
NOTE: The username must be unique. If username sent by Idp is in email format, the email prefix will be used for username. The email prefix in this case must be | Identifies the Username (must be unique for each user) value: http://schemas.xmlsoap.org/ws/2005/05/identity/claims/upn or upn
|
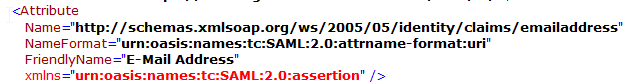
IdP Email Parameter | Identifies the email of the user (must be unique) Default value: mail | Identifies the email of the user (must be unique) http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress or emailaddress
|
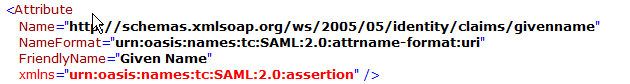
IdP Given Name Parameter | Identifies the given name of the user Default value: givenName | Identifies the given name of the user. http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname or givenname
|
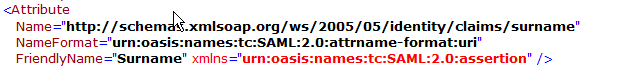
IdP Surname Parameter | Identifies the surname of the user Default value: sn | Identifies the sur name of the user http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname or surname
|
| IdP Log Out URL (Optional) | URL for logging out of IdP | URL for logging out of IdP Note: For this setting to be effective, you must also add a setting to the FileCloud config file:
|
| Limit Logon to IdP Group (available in FileCloud Version 19.1 and higher) | IdP Group Name
| IdP Group Name
|
| Show the IdP Logon Screen | Identifies which Logon screen the user will see:
| Identifies which Logon screen the user will see:
|
| IdP Metadata | Identity Provider metadata in XML Format | Federation metadata in xml format |
| SSO Error Message (Optional) Added in FileCloud 20.1 | Custom error message that appears when a signin is invalid. Enter in HTML format. | Custom error message that appears when a signin is invalid. Enter in HTML format. |
Allow Account Signups Added in FileCloud 20.1 | When TRUE, during the login process, if the user account does not exists, a new FileCloud user account is created automatically. | When TRUE, during the login process, if the user account does not exists, a new FileCloud user account is created automatically. |
Automatic Account Approval Added in FileCloud 20.1 | This setting works with the Allow Account Signups setting to determine:
See Integrating Multiple IDPs for help configuring multiple IDPs with automatic account approval settings specific to each one. | This setting works with the Allow Account Signups setting to determine:
|
| Enable ADFS | No | Yes |
| User login token expiration match Idp expiration | If enabled the user token expiration will be set based on Idp expiration settings If not enabled user token expiration will be set based on FileCloud Session Timeout Default: No (Not enabled) | If enabled the user token expiration will be set based on ADFS expiration settings If not enabled user token expiration will be set based on FileCloud Session Timeout Default: No (Not enabled) |
| Enable Browser-Only SSO Session Timeout Added in FileCloud 23.232.1 | If enabled, SSO session timeouts apply to browser sessions but not to client sessions. | If enabled, SSO session timeouts apply to browser sessions but not to client sessions. |
| Show the Idp Login Screen | If enabled, automatically redirect user to Idp log-in screen. | If enabled, automatically redirect user to Idp log-in screen. |
| Log Level | Set the Log mode for the SAML Calls. Default Value: prod (Do not use DEV for production systems) | Set the Log mode for the SAML Calls. Default Value: prod (Do not use DEV for production systems) |
Use the following URL (Entity ID) to register FileCloud as an SP with IdP or ADFS. The URL below also provides the metadata of the FileCloud SP:
http://<Your Domain>/simplesaml/module.php/saml/sp/metadata.php/default-sp
You can customize the user log-in screen to display the SSO log-in option along with the direct log-in option or to only display the SSO log-in.
To display the SSO log-in option along with the direct log-in option:
- From the left navigation pane, click Customization.
Select the General tab, and then the Login sub-tab.
- Check Show SSO Link and Show Login Options.
- Save your changes.
Now, when users access the user portal log-in page, they will see: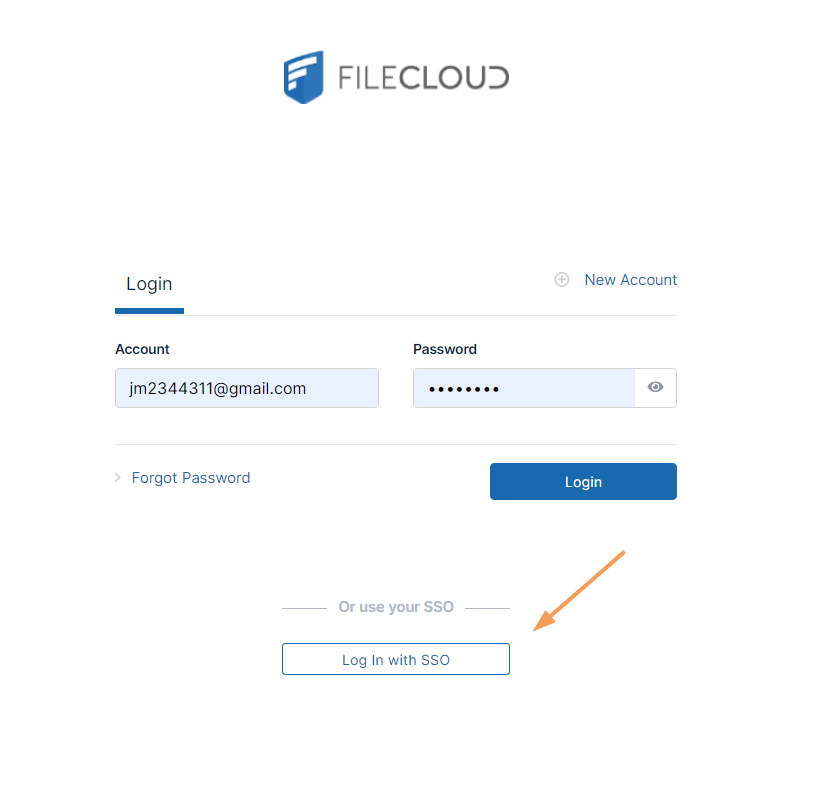
On clicking the Single Sign-On link on the login page, the user is redirected to the SAML SSO Service web page.
The SSO log-in option in the admin portal:
FileCloud admin interface also supports Single Sign-On.
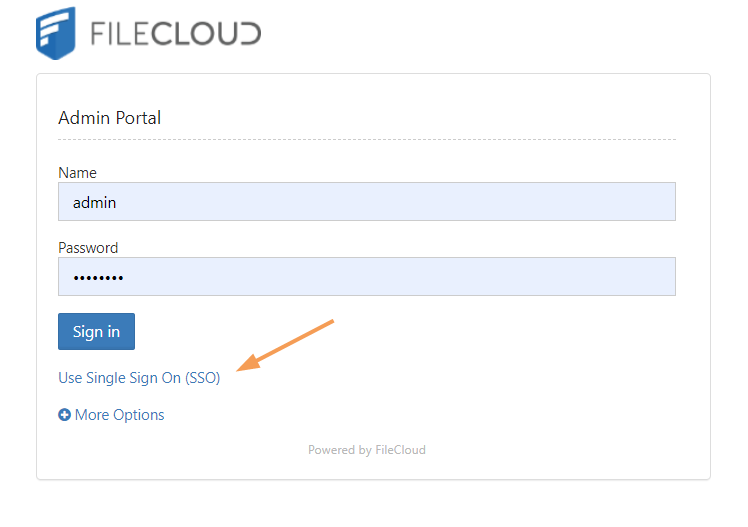
Default admin portal log-in screen
To only display the SSO log-in option:
In order to skip the FileCloud login page and send the user directly to the SAML SSO page you must add a setting to the cloudconfig.php file, as shown below. You can configure this option for the user portal login page and the admin portal login page.
To only display the SSO log-in option in the user portal:
This configuration option is available starting with FileCloud Version 19.3, It supports skipping the login page when the user accesses FileCloud with a domain name or with a full URL.
In the admin portal, go to Customization, and select the General tab, and then the Login sub-tab.
- Check Show SSO Link and Show Login Options, and save your changes.
- Open the configuration file:
Windows: XAMPP DIRECTORY/htdocs/config/cloudconfig.php
Linux: /var/www/config/cloudconfig.php To only display the SSO log-in option:
define("TONIDOCLOUD_SSO_DIRECT_ONLY", "1");When users enter the log-in page they will see:
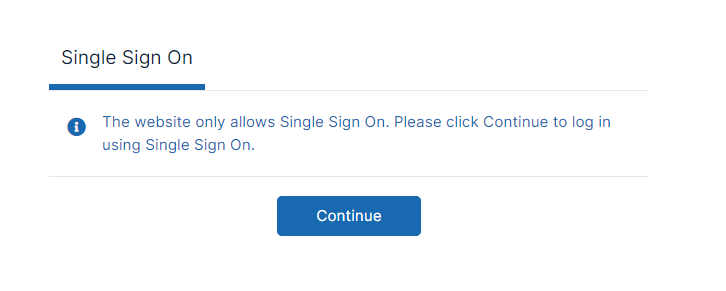
To return to displaying other log-in options:
define("TONIDOCLOUD_SSO_DIRECT_ONLY", "0");
To display only SSO log-in in the admin portal:
Starting with Version 20.1, FileCloud supports skipping the login page when the admin accesses FileCloud with a domain name or with a full URL.
- Open the configuration file:
Windows: XAMPP DIRECTORY/htdocs/config/cloudconfig.php
Linux: /var/www/config/cloudconfig.php To only display the SSO log-in option:
Enter:
define ("TONIDOCLOUD_SSO_DIRECT_ONLY_ADMIN", "1");An earlier version of this option is also effective in versions of FileCloud prior to 20.1, but this redirect is only effective if the user specifies a domain name rather than a full URL. Instead of the above setting, use:
define("TONIDOCLOUD_SSO_DIRECT_ADMIN", "1");
To enable secure cookies when using SimpleSAML to authenticate, proceed on the following.
- Open the SimpleSAML configuration file:
Windows: XAMPP DIRECTORY/htdocs/thirdparty\simplesaml\config\config.php
Linux: /var/www/config/thirdparty/simplesaml/config/config.php Change session.cookie.secure from FALSE to TRUE:
'session.cookie.secure' => true,
(Optional) For better cookie security set the session.cookie.samesite attribute to Strict or Lax according to the environment's needs.
If the FileCloud site is embedded in an external site, it may be necessary to leave this setting null or set it to None to enable cookie sharing with the external site.'session.cookie.samesite' => 'Strict',
Avoid Open Redirect
FileCloud may be vulnerable to an open redirect when SSO is implemented.
- An open redirect is an application vulnerability that takes a parameter and redirects the user to the supplied parameter value without any validation.
This can be avoided by configuring the following setting:
Navigate to the following directory:
<FileCloud WEB ROOT>/thirdparty/simplesaml/config
Open the following file for editing:
config.php
Add the following line:
'trusted.url.domains' => array()
Restrict the Available Admin Login Resources
The FileCloud admin portal can possibly allow 2 administrative login interfaces:
- One at admin API interface: /admin
- One at simpleSAML admin resource: /simpleSAML.
This can be avoided by changing the log level to "PROD" in SSO settings under settings in FileCloud admin interface. This will disable the SSO admin page under simpleSAML.
The password to the SSO admin page under /simpleSAML can be changed under 'auth.adminpassword' key in <FileCloud WEB ROOT>/thirdparty/simplesaml/config/config.php
Troubleshooting
Issues that you may encounter and how to resolve them.
Issue
FileCloud is hosted behind a Proxy
Solution
When FileCloud is hosted behind a proxy server, SAML will not automatically work.
Go to <FileCloud WEB ROOT>/thirdparty/simplesaml/config/filecloudconfig.php
Add Proxy Server Information here.
Format is as follows user:password@yourproxyserverurl.com
define("TONIDOCLOUD_SAML_PROXY", "ADD PROXY INFO HERE");
Issue
System Timezone Settings
Solution
After setting SAML log level to DEV. Log file will be created under <FileCloud WEB ROOT>/thirdparty/simplesaml/log/simplesamlphp.log
SimpleSAML_Error_Exception: Error 2 - strftime(): It is not safe to rely on the system's timezone settings. You are *required* to use the date.timezone setting or the date_default_timezone_set() function.
Solution: date.timezone setting must be set explicitly in php.ini
Issue
FileCloud is hosted behing a reverse proxy
Solution
When FileCloud is hosted behind a proxy server, SAML will not automatically work.
Go to <FileCloud WEB ROOT>/thirdparty/simplesaml/config/config.php
set the base url to 'baseurlpath' => 'http(s)://YOURFILECLOUDOMAIN/simplesaml/'
Issue
Debug page login
Solution
https://YOURFILECLOUDDOMAIN/simplesaml/module.php/core/frontpage_welcome.php
Issue
FileCloud in HA (High Availability) environment with multiple servers
Solution
In this scenario, SimpleSAML will most likely not work with default configuration and will require to run Memcache to manage the session.
Go to <FileCloud WEB ROOT>/thirdparty/simplesaml/config/config.php
set the store.type => memcache
and set
'memcache_store.servers' => array(
array(
array('hostname' => 'localhost'),
),
),
where 'localhost' must be replaced with IP of memcache server as appropriate.
Issue
Autofill Username or Email on the IDP screen when configured:
TONIDOCLOUD_SAML_DOMAINS_ALLOWED
Solution
When autofill will only work when username or email address is sent through POST from the FileCloud login page to IDP. Therefore, ensure that the IDP metadata accepts requests through only POST. For example, if the Idp Metadata contains the following 2 similar lines, remove the Redirect and only have the POST
<md:SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https://mailinator-raja.okta.com/app/mailinatororg747392_myidp_1/exkgimvocj18Exx9g4x6/sso/saml"/>
<md:SingleSignOnService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://mailinator-raja.okta.com/app/mailinatororg747392_myidp_1/exkgimvocj18Exx9g4x6/sso/saml"/>
Integrating with other applications
- Integrate Auth0 SSO with Filecloud
- Integrate Microsoft Entra ID with FileCloud
- Integrate Centrify with FileCloud
- Integrate CYBERARK with FileCloud
- Integrate JumpCloud with FileCloud
- Integrate Okta with FileCloud
- Integrate OneLogin with FileCloud
- Integrate ADSelfService Plus with FileCloud
- Integrating Multiple IDPs
- Integrate Ping Identity SSO with Filecloud
- Setting Up and Configuring Certificates when Upgrading SSO
Override the default SSO port
To override the default port:
- Open cloudconfig.php:
Windows Location: XAMPP DIRECTORY/htdocs/config/cloudconfig.php
Linux Location: /var/www/config/cloudconfig.php Add the following line:
define("TONIDOCLOUD_SSO_FULLURL_OVERRIDE", "https://filecloud.test.com");
Use multiple memcache servers
In FileCloud Versions 20.3.2 and higher, you can use multiple memcache servers with SAML SSO to achieve high availability.
To use multiple memcache servers:
- Open cloudconfig.php:
Windows Location: XAMPP DIRECTORY/htdocs/config/cloudconfig.php
Linux Location: /var/www/config/cloudconfig.php - Add the following lines, including a hostname for each of the memcache servers.
In this example, the IP addresses of the servers are 79.97.83.70 and 79.97.83.71.
function SSO_MEMCACHED_SERVERS() { return [ [ ['hostname' => '79.97.83.70'], ['hostname' => '79.97.83.71'], ], ]; }